HTTP vs HTTPS

The topics of security & encryption continue to be big items for 2016. Keep your eyes open for more conversation on this topic, but for now, I want to focus on a simple form of encryption that you’ve probably used without realizing it: HTTPS.
HyperText Transfer Protocol (HTTP) is a protocol for sending and receiving information across the Internet. Simply put, it’s one of the many ways computers can communicate to each other. HTTP is commonly used to access web pages, as a server communicates with your web browser and vice-versa. Perhaps you’ve noticed the prefix in various links on the web: http://bpimediagroup.com, for example.
Secure HyperText Transfer Protocol (HTTPS) is a combination of HTTP and SSL/TLS protocol. This extra protocol allows for the secure, encrypted transfer of sensitive information such as banking data, payment gateways, personal information, and even emails. You’ll see these in Gmail, Facebook, and anywhere that you’re providing payment information.
Many modern web browsers highlight HTTPS in URLs to help users have an easier understanding of the site’s security:
If a certificate is present but expired (they stay valid for a year), most browsers will alert you so you can make an informed decision.
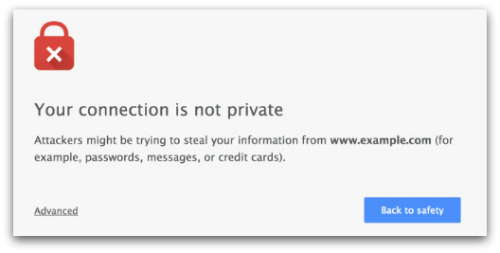
As our Internet becomes increasingly connected, I expect we’ll see more flags like the above to deter visitors to insecure or potentially malicious websites.
In Conclusion
At the end of the day, there are lots of factors to consider when it comes to cybersecurity. Given the option, always use HTTPS when dealing with anything potentially sensitive. But it’s also important to understand that simply having a secure connection to transfer you information does not ensure that you’re completely safe, however. Just look at the Target breach: all of that user data was securely captured. And all of it was then leaked from there data center where it was stored!
As the conversation and standards regarding security, encryption, and private data continues to evolve alongside the emerging markets, so the exploits, breaches, and overall confusion. All we can do as individuals is to make informed decisions about our engagement with these technologies.



